首先使用exeinfope查壳

发现并没有壳,但是是64位的linux的ELF文件,可能会涉及大小端问题
有ida反编译后找到mian函数进行反编译

v5和s2的地址临近
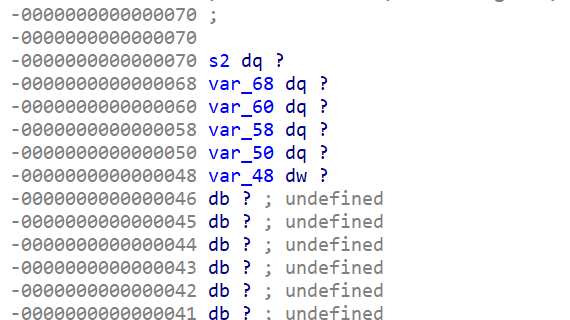
所以v5其实是s2[5]
python脚本如下
# 硬编码的字节序列,对应于C代码中的s2数组和v5变量# 这里我们将每个64位整数按小端字节序转换为字节序列encrypted_bytes = [ 0x35, 0x29, 0x02, 0x35, 0x3E, 0x35, 0x0F, 0x60, # s2[0] 0x20, 0x06, 0x64, 0x26, 0x65, 0x1A, 0x61, 0x77, # s2[1] 0x5A, 0x64, 0x68, 0x60, 0x53, 0x60, 0x20, 0x4E, # s2[2] 0x6B, 0x21, 0x67, 0x54, 0x7E, 0x71, 0x51, 0x64, # s2[3] 0x75, 0x60, 0x51, 0x64, 0x73, 0x05, 0x65, 0x21, # s2[4] 0x61, 0x4A # v5]# 循环使用的密钥key = "SEcRET7"# 解密函数def decrypt(encrypted, key): decrypted = "" key_length = len(key) for i, byte in enumerate(encrypted): decrypted_char = byte ^ ord(key[i % key_length]) decrypted += chr(decrypted_char) return decrypted# 解密并打印结果original_input = decrypt(encrypted_bytes, key)print(f"The original input was: {original_input}")



Comments 1 条评论
催更